侦查和扫描#
前言#
最近家里的电脑有时间打开了,就开始做下 GOAD 靶场实验,GOAD 靶场的 writeup 先根据作者的流程走,后期学完可以做些自我理解及补充。
环境搭建参考之前的博客:https://lca.xlog.app/game-of-active-directoryGOAD-yu-huan-jing-da-jian
做实验前,vm 虚拟机打个快照

启动所有机器
vargant up
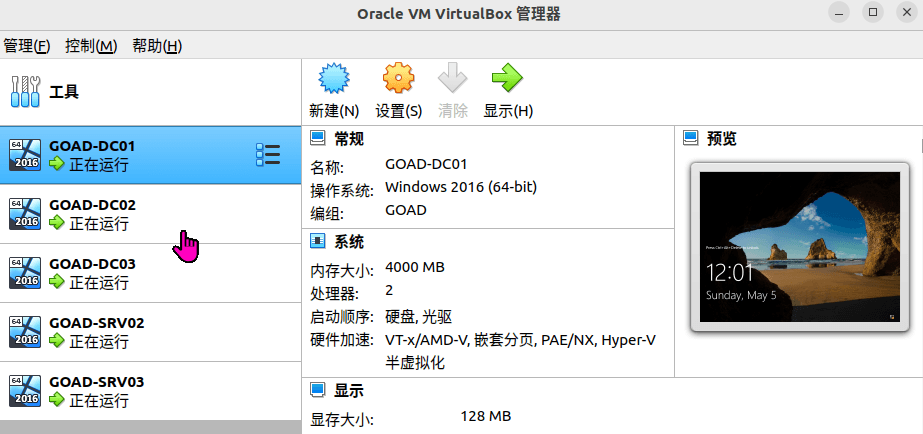
环境网络设置

ubuntu:承载了 virtualbox 的 vm 虚拟机 ip 段为:192.168.31.0/24 段
virtualbox:GOAD 靶场的的虚拟机 ip 段为 192.168.56.1/0 段
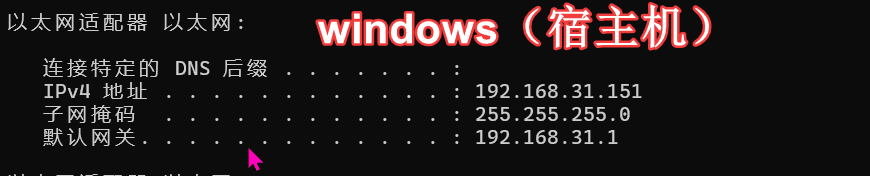
那么环境的整体访问路径为:
windows(宿主机 - ip:192.168.31.151)-> ubuntu(vm 虚拟机 - ip:192.168.31.142)-> GOAD 靶场(virtualbox 虚拟机 - ip:192.168.56.1/24 段)
本想用 kali 作为攻击机器,但就像之前文章评论说的那样,会无法访问,需要做代理出来测试,但开启 kali 会占内存,我的宿主机内存只有 32G,如果再开一台 kali,靶机就会因内存不足,报错。
宿主机的 cpu 也会飙升。

所以就直接再 ubuntu 上直接进行攻击利用,如果后期 ubuntu 机器不满足攻击需求另说吧!
网络枚举#
cme
# 安装cme
sudo snap install crackmapexec
# cme smb扫描
crackmapexec smb 192.168.56.0/24

cme 扫描的结果入上图,返回了一些有用的信息,获取了所有靶机的 ip、名称和域信息
SMB 192.168.56.10 445 KINGSLANDING [*] Windows 10.0 Build 17763 x64 (name:KINGSLANDING) (domain:sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 192.168.56.12 445 MEEREEN [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:MEEREEN) (domain:essos.local) (signing:True) (SMBv1:True)
SMB 192.168.56.22 445 CASTELBLACK [*] Windows 10.0 Build 17763 x64 (name:CASTELBLACK) (domain:north.sevenkingdoms.local) (signing:False) (SMBv1:False)
SMB 192.168.56.11 445 WINTERFELL [*] Windows 10.0 Build 17763 x64 (name:WINTERFELL) (domain:north.sevenkingdoms.local) (signing:True) (SMBv1:False)
SMB 192.168.56.23 445 BRAAVOS [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:BRAAVOS) (domain:essos.local) (signing:False) (SMBv1:True)
- north.sevenkingdoms.local(2 个 ip)
- CASTELBLACK 192.168.56.22
- WINTERFELL 192.168.56.11
- sevenkingdoms.local(1 个 ip)
- KINGSLANDING 192.168.56.10
- essos.local(2 个 ip)
- MEEREEN 192.168.56.12
- BRAAVOS 192.168.56.23
从拓扑图中也清楚知道,GOAD 靶机有三个域。也从 cme 的扫描结果中知道,DC 的签名都为 True(signing),在真实环境中,为了防止 NTLM 中继,必须将所有的签名设置为 True。
查找 DC 的 ip#
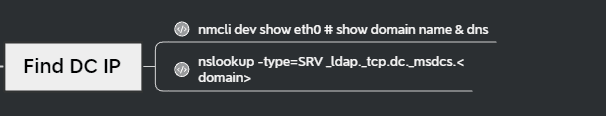
可以使用 nslookup 执行 DNS 查询从而列出 DC 的相关信息
nslookup -type=srv _ldap._tcp.dc._msdcs.sevenkingdoms.local 192.168.56.10
- nslookup:dns 查询工具
- -type=srv:指定查询 SRV 记录,SRV 记录是一种用于标识特定服务的 DNS 记录类型。
_ldap._tcp.dc._msdcs.sevenkingdoms.local:需要查询的主机名,用于查找在 "sevenkingdoms.local" 域中提供 LDAP 服务的域控制器的相关信息- 查询的 DNS 服务器的 IP 地址
查询 sevenkingdoms.local

查询 north.sevenkingdoms.local
nslookup -type=srv _ldap._tcp.dc._msdcs.north.sevenkingdoms.local 192.168.56.10

查询 essos.local
nslookup -type=srv _ldap._tcp.dc._msdcs.north.essos.local 192.168.56.10

设置 /etc/hosts 和 kerberos#
在 linux 环境中使用 kerberos,需要进行一些设置
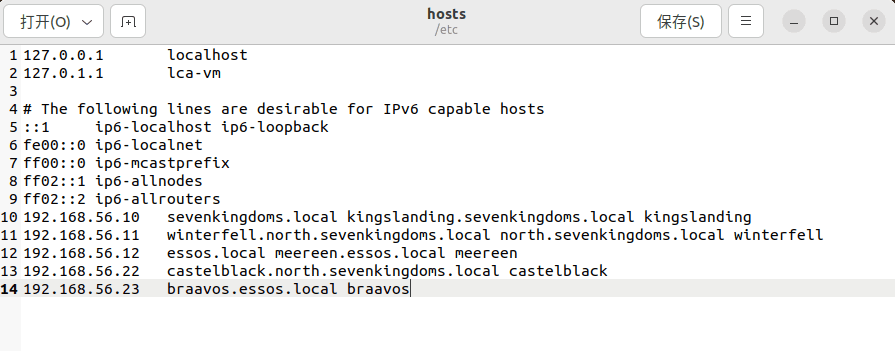
1、配置 /etc/hosts 文件来设置 DNS
# /etc/hosts
# GOAD
192.168.56.10 sevenkingdoms.local kingslanding.sevenkingdoms.local kingslanding
192.168.56.11 winterfell.north.sevenkingdoms.local north.sevenkingdoms.local winterfell
192.168.56.12 essos.local meereen.essos.local meereen
192.168.56.22 castelblack.north.sevenkingdoms.local castelblack
192.168.56.23 braavos.essos.local braavos
安装 kerberos linux 客户端
sudo apt install krb5-user

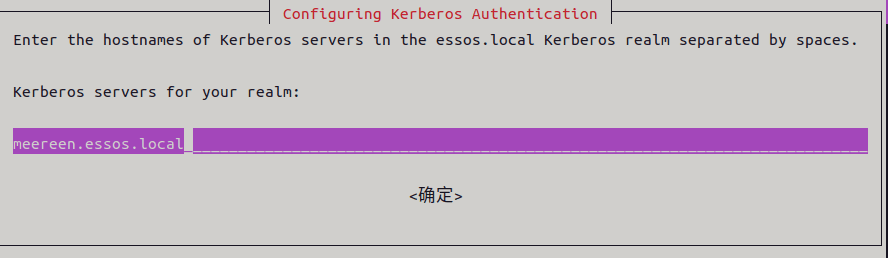
admin_server 设置为 meereen.essos.local
如果 krb5-user 已经安装,或者需重新配置,可以使用 dpkg-reconfigure 或修改 /etc/krb5.conf 文件进行重新配置,内容如下:
sudo gedit /etc/krb5.conf
[libdefaults]
default_realm = essos.local
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
fcc-mit-ticketflags = true
[realms]
north.sevenkingdoms.local = {
kdc = winterfell.north.sevenkingdoms.local
admin_server = winterfell.north.sevenkingdoms.local
}
sevenkingdoms.local = {
kdc = kingslanding.sevenkingdoms.local
admin_server = kingslanding.sevenkingdoms.local
}
essos.local = {
kdc = meereen.essos.local
admin_server = meereen.essos.local
}
kerberos 设置完成后,可以尝试是否可以获取 TGT 票据了。
下载:
Impacket is a collection of Python classes for working with network protocols.
sudo pip3 install .
sudo python3 setup.py install
getTGT.py essos.local/khal.drogo:horse
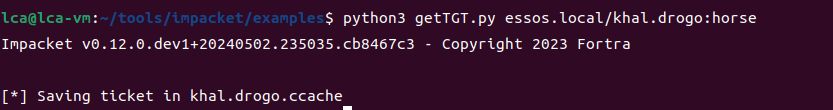
export KRB5CCNAME=/home/lca/tools/impacket/examples/khal.drogo.ccache
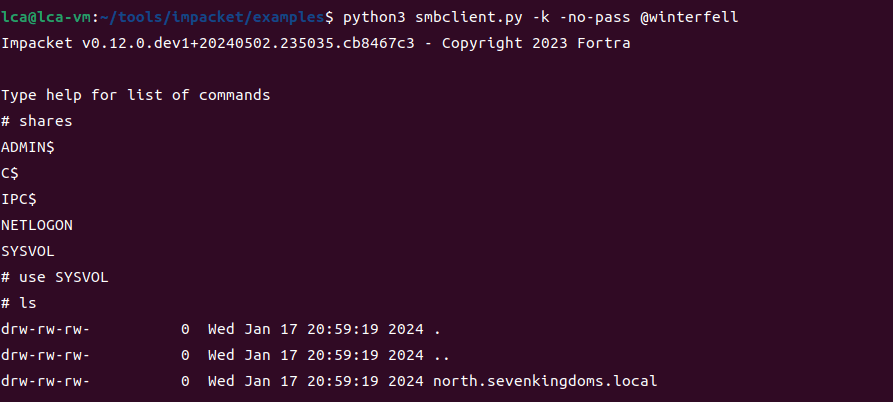
python3 smbclient.py -k @braavos.essos.local
Impacket v0.12.0.dev1+20240502.235035.cb8467c3 - Copyright 2023 Fortra
Type help for list of commands
# shares
ADMIN$
all
C$
CertEnroll
IPC$
public
# use C$
# ls
drw-rw-rw- 0 Thu Feb 14 19:42:10 2019 $Recycle.Bin
-rw-rw-rw- 384322 Fri Feb 15 03:38:48 2019 bootmgr
-rw-rw-rw- 1 Fri Feb 15 03:38:48 2019 BOOTNXT
-rw-rw-rw- 1014 Thu Jan 18 00:00:49 2024 dns_log.txt
drw-rw-rw- 0 Wed Jan 17 07:27:46 2024 Documents and Settings
drw-rw-rw- 0 Wed Jan 17 22:04:13 2024 inetpub
-rw-rw-rw- 1476395008 Sun May 5 23:00:57 2024 pagefile.sys
drw-rw-rw- 0 Thu Feb 14 20:19:12 2019 PerfLogs
drw-rw-rw- 0 Wed Jan 17 23:07:58 2024 Program Files
drw-rw-rw- 0 Thu Jan 18 00:28:34 2024 Program Files (x86)
drw-rw-rw- 0 Thu Jan 18 00:17:10 2024 ProgramData
drw-rw-rw- 0 Tue Jan 16 23:28:06 2024 Recovery
drw-rw-rw- 0 Wed Jan 17 22:31:30 2024 setup
drw-rw-rw- 0 Thu Jan 18 00:32:16 2024 shares
drw-rw-rw- 0 Sun May 5 15:01:26 2024 System Volume Information
drw-rw-rw- 0 Wed Jan 17 21:53:12 2024 tmp
drw-rw-rw- 0 Wed Jan 17 23:57:19 2024 Users
drw-rw-rw- 0 Wed Jan 17 22:05:24 2024 Windows
如上,kerberos 就设置好了
通过 unset 票据
unset KRB5CCNAME
测试其他几个域
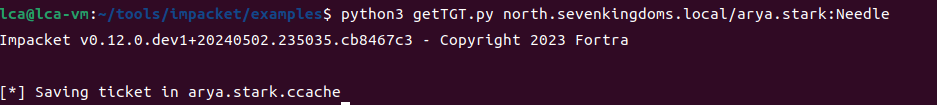
export KRB5CCNAME=/home/lca/tools/impacket/examples/arya.stark.ccache
python3 smbclient.py -k -no-pass @winterfell.north.servenkingdoms.local
Impacket v0.12.0.dev1+20240502.235035.cb8467c3 - Copyright 2023 Fortra
[-] [Errno Connection error (winterfell.north.servenkingdoms.local:445)] [Errno -3] Temporary failure in name resolution

不知道为什么 Kerberos 在 Winterfell 使用完整 FQDN 时无法工作,但通过仅设置 Winterfell 而不是 winterfell.north.sevenkingdoms.local 就没问题了。
nmap 扫描#
安装 nmap
sudo apt install nmap
通过 nmap 来进行扫描,使用如下参数扫描
nmap -Pn -p- -sC -sV -oA full_scan_goad 192.168.56.10-12,22-23
参数如下:
- -Pn:不进行 ping 扫描
- -p-:全端口扫描,1-65535
- -sC:运行默认的探测脚本
- -sV:对指定端口执行服务版本检测
- -oA:输出三种格式的结果
nmap 扫描结果如下:
# Nmap 7.80 scan initiated Sun May 5 16:44:49 2024 as: nmap -Pn -p- -sC -sV -oA full_scan_goad 192.168.56.10-12,22-23
Nmap scan report for sevenkingdoms.local (192.168.56.10)
Host is up (0.0011s latency).
Not shown: 65505 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-05 08:45:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-01-17T13:15:48
|_Not valid after: 2025-01-16T13:15:48
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-01-17T13:15:48
|_Not valid after: 2025-01-16T13:15:48
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-01-17T13:15:48
|_Not valid after: 2025-01-16T13:15:48
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:kingslanding.sevenkingdoms.local
| Not valid before: 2024-01-17T13:15:48
|_Not valid after: 2025-01-16T13:15:48
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local
| Not valid before: 2024-01-16T12:49:01
|_Not valid after: 2024-07-17T12:49:01
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-01-15T06:56:16
|_Not valid after: 2027-01-14T06:56:16
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
49711/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=5/5%Time=66374728%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: KINGSLANDING; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: KINGSLANDING, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:62:c4:af (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-05-05T08:48:40
|_ start_date: N/A
Nmap scan report for winterfell.north.sevenkingdoms.local (192.168.56.11)
Host is up (0.00079s latency).
Not shown: 65506 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-05 08:45:28Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-01-17T15:35:51
|_Not valid after: 2025-01-16T15:35:51
|_ssl-date: 2024-05-05T08:48:57+00:00; -1s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-01-17T15:35:51
|_Not valid after: 2025-01-16T15:35:51
|_ssl-date: 2024-05-05T08:48:57+00:00; 0s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-01-17T15:35:51
|_Not valid after: 2025-01-16T15:35:51
|_ssl-date: 2024-05-05T08:48:57+00:00; -1s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:winterfell.north.sevenkingdoms.local
| Not valid before: 2024-01-17T15:35:51
|_Not valid after: 2025-01-16T15:35:51
|_ssl-date: 2024-05-05T08:48:57+00:00; -1s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local
| Not valid before: 2024-01-16T12:59:52
|_Not valid after: 2024-07-17T12:59:52
|_ssl-date: 2024-05-05T08:48:57+00:00; -1s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-01-15T07:00:27
|_Not valid after: 2027-01-14T07:00:27
|_ssl-date: 2024-05-05T08:48:57+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49687/tcp open msrpc Microsoft Windows RPC
49694/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
54275/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=5/5%Time=6637472E%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: WINTERFELL; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: WINTERFELL, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:73:1f:da (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-05-05T08:48:43
|_ start_date: N/A
Nmap scan report for essos.local (192.168.56.12)
Host is up (0.00043s latency).
Not shown: 65508 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-05 08:46:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-01-17T13:55:53
|_Not valid after: 2025-01-16T13:55:53
|_ssl-date: 2024-05-05T08:48:57+00:00; 0s from scanner time.
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: ESSOS)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-01-17T13:55:53
|_Not valid after: 2025-01-16T13:55:53
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-01-17T13:55:53
|_Not valid after: 2025-01-16T13:55:53
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: essos.local, Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=meereen.essos.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:meereen.essos.local
| Not valid before: 2024-01-17T13:55:53
|_Not valid after: 2025-01-16T13:55:53
|_ssl-date: 2024-05-05T08:48:57+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=meereen.essos.local
| Not valid before: 2024-01-16T12:49:13
|_Not valid after: 2024-07-17T12:49:13
|_ssl-date: 2024-05-05T08:48:57+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-01-15T07:08:56
|_Not valid after: 2027-01-14T07:08:56
|_ssl-date: 2024-05-05T08:48:58+00:00; 0s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49681/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49711/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=5/5%Time=66374763%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: MEEREEN; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_nbstat: NetBIOS name: MEEREEN, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:c5:7e:aa (Oracle VirtualBox virtual NIC)
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-05-05T08:48:42
|_ start_date: 2024-05-05T04:02:06
Nmap scan report for castelblack.north.sevenkingdoms.local (192.168.56.22)
Host is up (0.0022s latency).
Not shown: 65516 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 15.00.2000.00
| ms-sql-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: CASTELBLACK
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: castelblack.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-05-05T07:22:58
|_Not valid after: 2054-05-05T07:22:58
|_ssl-date: 2024-05-05T08:48:57+00:00; -1s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: CASTELBLACK
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: castelblack.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
| Product_Version: 10.0.17763
|_ System_Time: 2024-05-05T08:48:42+00:00
| ssl-cert: Subject: commonName=castelblack.north.sevenkingdoms.local
| Not valid before: 2024-01-16T13:08:04
|_Not valid after: 2024-07-17T13:08:04
|_ssl-date: 2024-05-05T08:48:57+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-01-15T07:18:49
|_Not valid after: 2027-01-14T07:18:49
|_ssl-date: 2024-05-05T08:48:57+00:00; 0s from scanner time.
| tls-alpn:
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49695/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
49865/tcp open ms-sql-s Microsoft SQL Server
| ms-sql-ntlm-info:
| Target_Name: NORTH
| NetBIOS_Domain_Name: NORTH
| NetBIOS_Computer_Name: CASTELBLACK
| DNS_Domain_Name: north.sevenkingdoms.local
| DNS_Computer_Name: castelblack.north.sevenkingdoms.local
| DNS_Tree_Name: sevenkingdoms.local
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-05-05T07:22:58
|_Not valid after: 2054-05-05T07:22:58
|_ssl-date: 2024-05-05T08:48:57+00:00; -1s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port49865-TCP:V=7.80%I=7%D=5/5%Time=663747D6%P=x86_64-pc-linux-gnu%r(ms
SF:-sql-s,25,"\x04\x01\0%\0\0\x01\0\0\0\x15\0\x06\x01\0\x1b\0\x01\x02\0\x1
SF:c\0\x01\x03\0\x1d\0\0\xff\x0f\0\x07\xd0\0\0\0\0");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| ms-sql-info:
| 192.168.56.22:1433:
| Version:
| name: Microsoft SQL Server
| number: 15.00.2000.00
| Product: Microsoft SQL Server
|_ TCP port: 1433
|_nbstat: NetBIOS name: CASTELBLACK, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:96:f0:ff (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-05-05T08:48:44
|_ start_date: N/A
Nmap scan report for braavos.essos.local (192.168.56.23)
Host is up (0.00073s latency).
Not shown: 65516 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 15.00.2000.00
| ms-sql-ntlm-info:
| Target_Name: ESSOS
| NetBIOS_Domain_Name: ESSOS
| NetBIOS_Computer_Name: BRAAVOS
| DNS_Domain_Name: essos.local
| DNS_Computer_Name: braavos.essos.local
| DNS_Tree_Name: essos.local
|_ Product_Version: 10.0.14393
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-05-05T07:01:25
|_Not valid after: 2054-05-05T07:01:25
|_ssl-date: 2024-05-05T08:51:34+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=braavos.essos.local
| Not valid before: 2024-01-16T13:46:38
|_Not valid after: 2024-07-17T13:46:38
|_ssl-date: 2024-05-05T08:51:34+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=VAGRANT
| Subject Alternative Name: DNS:VAGRANT, DNS:vagrant
| Not valid before: 2024-01-15T07:29:16
|_Not valid after: 2027-01-14T07:29:16
|_ssl-date: 2024-05-05T08:51:34+00:00; 0s from scanner time.
| tls-alpn:
| h2
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49693/tcp open msrpc Microsoft Windows RPC
49712/tcp open msrpc Microsoft Windows RPC
49724/tcp open msrpc Microsoft Windows RPC
49769/tcp open msrpc Microsoft Windows RPC
49773/tcp open msrpc Microsoft Windows RPC
49896/tcp open ms-sql-s Microsoft SQL Server
| ms-sql-ntlm-info:
| Target_Name: ESSOS
| NetBIOS_Domain_Name: ESSOS
| NetBIOS_Computer_Name: BRAAVOS
| DNS_Domain_Name: essos.local
| DNS_Computer_Name: braavos.essos.local
| DNS_Tree_Name: essos.local
|_ Product_Version: 10.0.14393
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-05-05T07:01:25
|_Not valid after: 2054-05-05T07:01:25
|_ssl-date: 2024-05-05T08:51:34+00:00; 0s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port49896-TCP:V=7.80%I=7%D=5/5%Time=66374886%P=x86_64-pc-linux-gnu%r(ms
SF:-sql-s,25,"\x04\x01\0%\0\0\x01\0\0\0\x15\0\x06\x01\0\x1b\0\x01\x02\0\x1
SF:c\0\x01\x03\0\x1d\0\0\xff\x0f\0\x07\xd0\0\0\0\0");
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_nbstat: NetBIOS name: BRAAVOS, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:36:af:ca (Oracle VirtualBox virtual NIC)
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-05-05T08:51:30
|_ start_date: 2024-05-05T07:01:07
Post-scan script results:
| clock-skew:
| 0s:
| 192.168.56.10 (sevenkingdoms.local)
| 192.168.56.12 (essos.local)
|_ 192.168.56.23 (braavos.essos.local)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 5 16:51:34 2024 -- 5 IP addresses (5 hosts up) scanned in 404.39 seconds
美化 nmap 输出的 xml 格式
sudo apt install xsltproc
xsltproc full_scan_goad.xml -o full_scan_goad.html
firefox full_scan_goad.html
